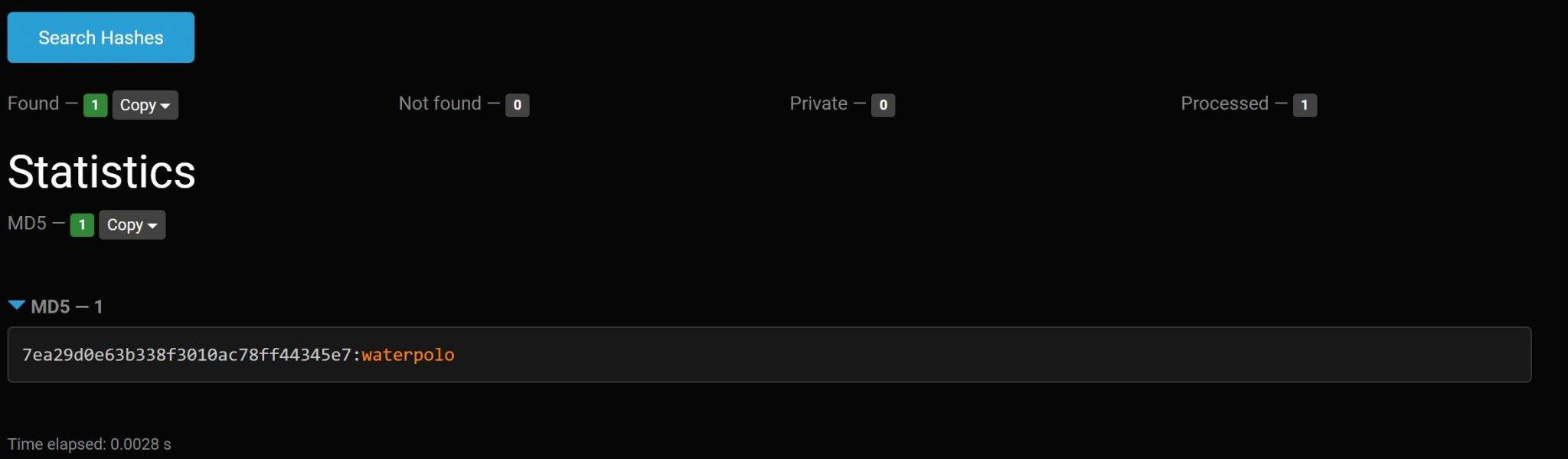
Fast online lm hash cracking. Use browser with frames support. CrackStation uses massive pre-computed lookup tables to crack password hashes. These tables store a mapping between the hash of a password, and the correct password for that hash. The hash values are indexed so that it is possible to quickly search the database for a given hash. Our WPA and hash cracking options:. Basic search (up to 1 hour) - we will search for common and default passwords only. Advanced search (1-3 hours) - we will automatically select suitable wordlists and keyspaces. Pro search (2-4 hours) - we will try even.
Hashes.org is a free online hash resolving service incorporating many unparalleled techniques. It is obvious that legacy methods of hash cracking are both time consuming and wasteful of resources. No matter the occasion, Cracker Barrel gift cards are perfect for your gifting needs. Gift cards are good for purchases in our restaurant, gift shop, or food orders online. Shop Gift Cards. Subscribe to Cracker Barrel News Good things come in emails so sign on up today.
A cryptographic hash function is an algorithm that can be run on data such as an individual file or a password to produce a value called a checksum. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. A cryptographic hash function is a special class of hash function that has certain properties which make it suitable for use in cryptography. Hash functions are generally irreversible (one-way), which means you can't figure out the input if you only know the output unless you try every possible input which is called a brute-force attack.

Generate your hash data online using md5, sha1, sha256, sha384, sha512, crc32, crc32b, gost, whirlpool, ripemd160, crypt (one way password hash with salt) HASH functions.
Use of Hash Functions
MD5
MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value. This md5 online generator calculate the md5 hash of a string, which from any input data creates a 32 character hexadecimal number. For example MD5 for 12345: 827ccb0eea8a706c4c34a16891f84e7bSHA1
SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function or algorithm which takes an input as a string and produces a 160-bit (20-byte) hash value known as a message digest typically generated as a hexadecimal number, 40 digits long.SHA256
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. SHA-256 algorithm generates an almost-unique, fixed size 256-bit (32-byte) hash. Applicable for password validation, digital signatures, hash authentication and anti-tamper.SHA384
A function used to calculate the SHA-384 hash of a data value. The hash will be returned as a hex-encoded string.SHA512
SHA512 is a cryptographic hash function that when applied to the provided input results in a 128-digit hexadecimal number.CRC32
Generates the cyclic redundancy checksum polynomial of 32-bit lengths of the string. This is usually used to validate the integrity of data being transmitted. Returns the crc32 checksum of string as an integer.CRC32b
CRC32b is an implementation of the consistency algorithm. The crc32b is the 32-bit Frame Check Sequence of ITU V.42 (used in Ethernet and popularised by PKZip).GOST Hash
GOST processes a variable-length message into a fixed-length output of 256 bits.Whirlpool
This is a 512-bit hash function.RIPEMD160
The RIPEND is an acronym for RACE Integrity Primitives Evaluation Message Digest. This set of hash functions was designed by open research community and generally known as a family of European hash functions. RIPEMD-160 is a 160-bit cryptographic hash function.Crypt
One-way string hashing. Crypt will return a hashed string using the standard Unix DES-based algorithm or alternative algorithms that may be available on the system.
Use of Online Hash Generator Tool
Online Hash Cracker Ntlmv2
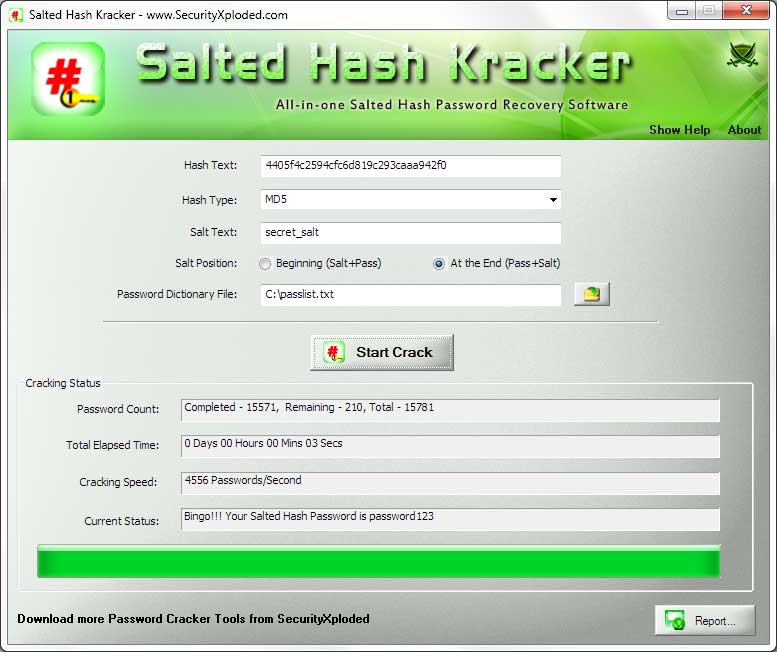
After you have generated hash data, you can simply click on 'Copy to Clipboard' or select all converted text and press 'Control-C' to copy, and then 'Control-V' to paste it back into your document.
Ntlm Cracker Online
Alternatively you can download generated hash data to text file simple click on the 'Download' button
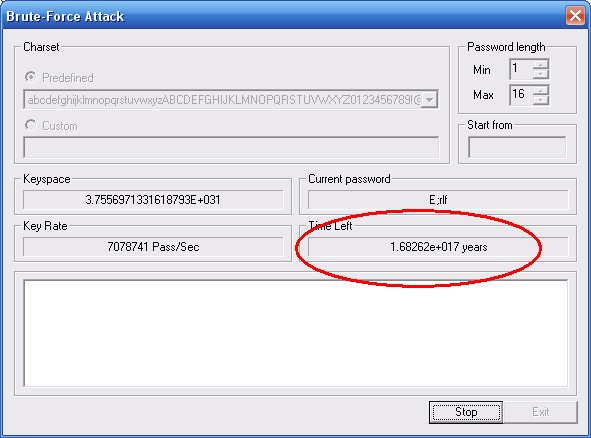
Fast online lm hash cracking. Use browser with frames support. CrackStation uses massive pre-computed lookup tables to crack password hashes. These tables store a mapping between the hash of a password, and the correct password for that hash. The hash values are indexed so that it is possible to quickly search the database for a given hash. Our WPA and hash cracking options:. Basic search (up to 1 hour) - we will search for common and default passwords only. Advanced search (1-3 hours) - we will automatically select suitable wordlists and keyspaces. Pro search (2-4 hours) - we will try even.
Hashes.org is a free online hash resolving service incorporating many unparalleled techniques. It is obvious that legacy methods of hash cracking are both time consuming and wasteful of resources. No matter the occasion, Cracker Barrel gift cards are perfect for your gifting needs. Gift cards are good for purchases in our restaurant, gift shop, or food orders online. Shop Gift Cards. Subscribe to Cracker Barrel News Good things come in emails so sign on up today.
A cryptographic hash function is an algorithm that can be run on data such as an individual file or a password to produce a value called a checksum. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. A cryptographic hash function is a special class of hash function that has certain properties which make it suitable for use in cryptography. Hash functions are generally irreversible (one-way), which means you can't figure out the input if you only know the output unless you try every possible input which is called a brute-force attack.
Generate your hash data online using md5, sha1, sha256, sha384, sha512, crc32, crc32b, gost, whirlpool, ripemd160, crypt (one way password hash with salt) HASH functions.
Use of Hash Functions
MD5
MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value. This md5 online generator calculate the md5 hash of a string, which from any input data creates a 32 character hexadecimal number. For example MD5 for 12345: 827ccb0eea8a706c4c34a16891f84e7bSHA1
SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function or algorithm which takes an input as a string and produces a 160-bit (20-byte) hash value known as a message digest typically generated as a hexadecimal number, 40 digits long.SHA256
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. SHA-256 algorithm generates an almost-unique, fixed size 256-bit (32-byte) hash. Applicable for password validation, digital signatures, hash authentication and anti-tamper.SHA384
A function used to calculate the SHA-384 hash of a data value. The hash will be returned as a hex-encoded string.SHA512
SHA512 is a cryptographic hash function that when applied to the provided input results in a 128-digit hexadecimal number.CRC32
Generates the cyclic redundancy checksum polynomial of 32-bit lengths of the string. This is usually used to validate the integrity of data being transmitted. Returns the crc32 checksum of string as an integer.CRC32b
CRC32b is an implementation of the consistency algorithm. The crc32b is the 32-bit Frame Check Sequence of ITU V.42 (used in Ethernet and popularised by PKZip).GOST Hash
GOST processes a variable-length message into a fixed-length output of 256 bits.Whirlpool
This is a 512-bit hash function.RIPEMD160
The RIPEND is an acronym for RACE Integrity Primitives Evaluation Message Digest. This set of hash functions was designed by open research community and generally known as a family of European hash functions. RIPEMD-160 is a 160-bit cryptographic hash function.Crypt
One-way string hashing. Crypt will return a hashed string using the standard Unix DES-based algorithm or alternative algorithms that may be available on the system.
Use of Online Hash Generator Tool
Online Hash Cracker Ntlmv2
After you have generated hash data, you can simply click on 'Copy to Clipboard' or select all converted text and press 'Control-C' to copy, and then 'Control-V' to paste it back into your document.
Ntlm Cracker Online
Alternatively you can download generated hash data to text file simple click on the 'Download' button
Online Hash Cracker Free
You can upload data text file to generated various hash data. Mighty long fall at yokohama stadium dvd download torrent.
Online Hash Crackers
Template brosur sekolah lipat 3 cdr untuk. If you like this tool and helpful to your work, then please recommend it to you friends and family who would also find it useful. Share it to your favorite social media like facebook, twitter etc.
